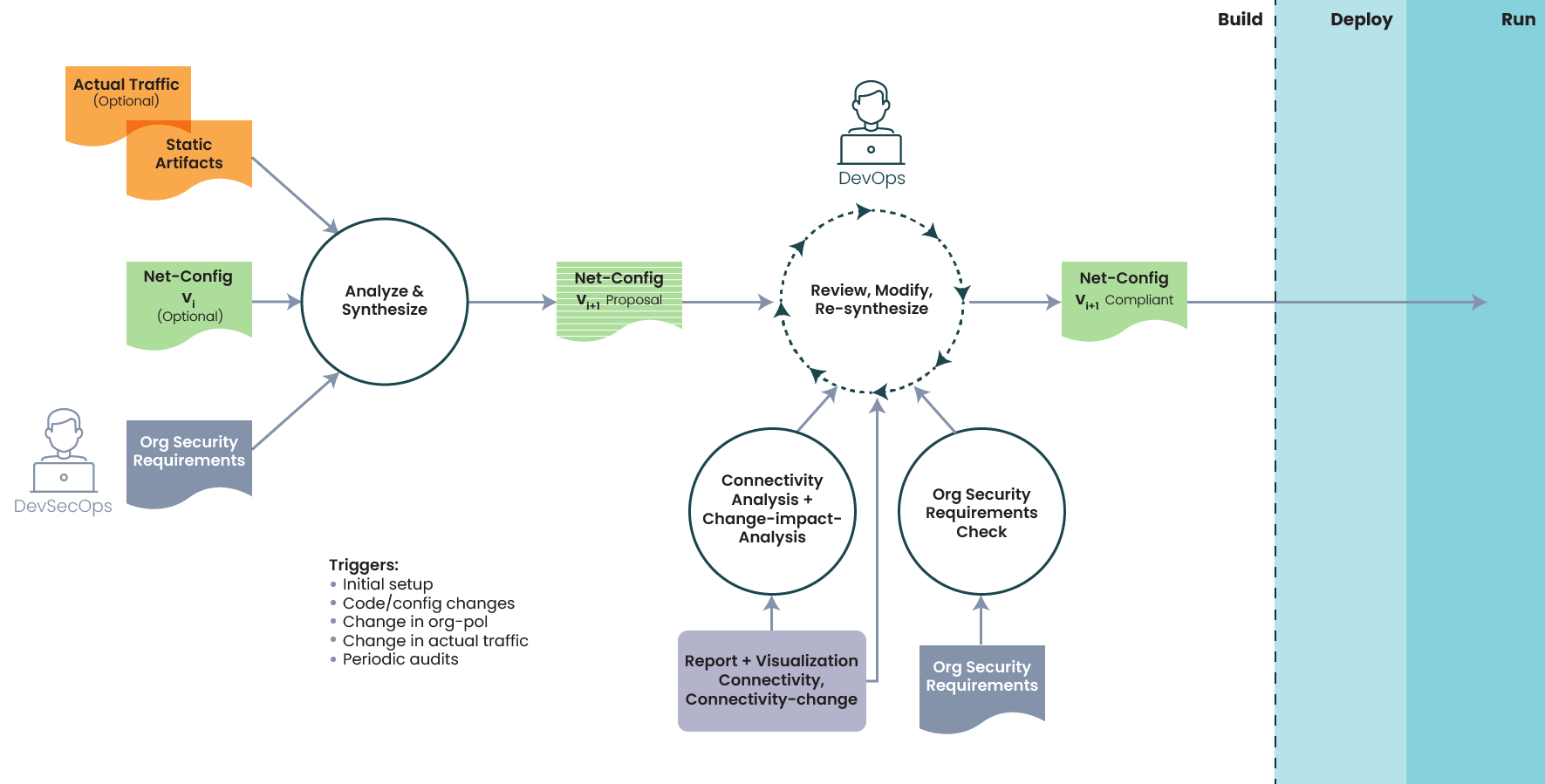
This project seeks to simplify the experience of creating and maintaining Kubernetes (K8s) network policies for zero-trust environments. When creating and managing K8s network policies, it can be difficult for users to enable just the right amount of connectivity. To help meet this challenge, we propose a solution for automating the generation of network policies without having to run the applications’ code. Our solution can be integrated into the application’s CI/CD pipeline, ensuring network policies get updated whenever the required cluster connectivity changes. The overall flow of the solution is presented below.
The flow consists of two stages:
- Automatic synthesis stage - Analyzes application configuration files and takes into account existing network configuration, actual cluster traffic, and baseline requirements. This stage of the flow also proposes updated network connectivity restrictions in the form of NetworkPolicy resources.
- Review and modify stage - The proposed network connectivity is presented to the DevOps team for their review. The presentation can be graphic, a concise textual report, or simply the actual NetworkPolicy YAML files. The presentation also includes a semantic diff of connectivity changes from the currently deployed configuration. Users can make changes to the proposed connectivity and these changes are then checked against baseline requirements. Only approved changes get deployed to the live cluster.
Our main GitHub Org page contains the source code for all components in the above flow (shown as solid circles). In particular, it contains the following repos:
- cluster-topology-analyzer - Scans a GitHub repo and extracts required network links from configuration files.
- netpol-synthesizer - Synthesizes a set of K8s network policies from the list of required network links and a set of baseline requirements.
- network-config-analyzer - Allows showing synthesized connectivity as a set of firewall rules. Can also produce connectivity diff between two network configurations.
- baseline-rules-verifier - Checks whether synthesized connectivity satisfies a set of baseline requirements.
- baseline-rules - Contains several examples of baseline requirements.
See CI Integration to learn how to integrate the above components into a CI/CD pipeline.